SHREE LEARNING ACADEMY
Replay Attack
A replay attack refers to a scenario where a malicious actor intercepts and duplicates network traffic by retransmitting it, with the intention of using it to gain unauthorized entry into a system. Typically, the attacker targets the communication between a client and server during the authentication process. In the event that a hacker manages to intercept authentication traffic, particularly the packets containing login credentials that may include certificates, token responses, or biometric data, they may use a replay attack to gain entry into a system by duplicating and resending the captured packets.
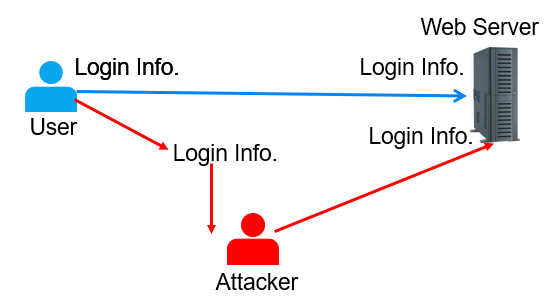
The replay attack illustrated in this figure involves the client sending its logon credentials to the server, while a malicious actor intercepts and listens in on this transmission. Later on, the attacker can replay the captured authentication packets towards the server, allowing them to forge a logon attempt as if they were the original client. In the event that a replay attack is successful, the malicious actor is able to acquire the same level of access as the legitimate user who provided the authentication information. Thankfully, numerous replay-protection mechanisms are employed by modern operating systems, networks, protocols, services, and applications to actively prevent such attacks.
Replay Attack Measures
Typical measures to thwart replay attacks involve packet sequencing, time stamps, challenge-response, and ephemeral session encryption.
Packet sequencing
Packet sequencing, for instance, verifies that any packet received out of order (or beyond an acceptable time frame) is rejected and disregarded.Packet time stamps
Packet time stamps, on the other hand, guarantee that any packet arriving beyond a particular time frame is rejected and disregarded. Kerberos serves as an excellent example of this, as it uses time stamps to eliminate the threat of replay attacks.Challenge-response
Challenge-response is an authentication method that involves the server generating and providing a random number challenge to the client attempting to connect. The client then employs both the challenge number and the hash of the user's password (or any other authentication factor) to produce a response. After generating the response, the client sends it back to the server, which then compares it with the anticipated response generated by using the challenge number and the credentials retrieved from the user account database. Given that each challenge is chosen at random and is valid only once, replay attacks are infeasible.
Ephemeral session key
An ephemeral session key is the application of DHE or ECDHE ("Diffie-Hellman") to generate session-specific symmetric encryption keys that are random, nonrepeating, non-reusable, and non-predictable. If the specified requirements are met, then every authentication session will be encrypted and the encryption will only be valid for a single use. This approach can effectively prevent replay attacks and is considered a dependable method.
Wireless Replay Attacks
While initial authentication abuse remains a common target, replay attacks in wireless environments may also take various other forms. One method is to capture a standard client's new connection request and replay it to deceive the base station into responding as though a different client had requested a new connection. Another type of wireless replay attack involves targeting the base station with connection or resource requests that are repeatedly transmitted, causing it to become preoccupied with managing new connections instead of maintaining and servicing existing ones, resulting in a DoS (denial of service) scenario.
To prevent wireless replay attacks, it's important to maintain up-to-date firmware on the base station and utilize a wireless-focused NIDS (network intrusion detection system). By implementing a W-IDS or W-NIDS, potential abuses can be detected, and administrators can be quickly alerted to the situation.
Test Yourself
Take Free Quiz
Watch our Video Tutorial