SHREE LEARNING ACADEMY
Denial of Service (DoS) Attacks
Denial of Service (DoS)
A denial of service (DoS) attack is designed to prevent a system from carrying out legitimate activities or responding to legitimate traffic. There are two primary types of DoS attacks. The first type exploits vulnerabilities, errors, or standard features of software to cause a system to become unresponsive, freeze, consume all resources, etc. As a result, the targeted computer is unable to perform any legitimate tasks. The second type of attack involves overwhelming the victim's communication channels with irrelevant network traffic, such as fake responses to non-existent requests, incomplete establishment of a TCP session, or repeated requests for data from a system. This leads to the targeted computer being unable to send or receive valid network communications, thereby preventing it from performing normal operations or services.
Denial of Service (DoS) is not a single attack, but a group of attacks that belong to the same category. These attacks may target weaknesses in the operating system software or installed applications, services, or protocols. Some attacks may specifically target protocols such as User Datagram Protocol (UDP), Transmission Control Protocol (TCP), Internet Protocol (IP), and Internet Control Message Protocol (ICMP).
DoS attacks are generally conducted between a single attacker and a single victim, but they may not always follow such a straightforward approach. Often, DoS attacks involve utilizing an intermediary system, which is usually an unwitting and unaware participant, to conceal the attacker's identity from the victim. Sending attack packets directly to a victim makes it possible for the victim to identify the attacker. However, the use of spoofing can make it more challenging, though not entirely impossible.
Distributed Denial of Service (DDoS)
The upcoming form of DoS attacks is referred to as distributed denial of service (DDoS) attacks. In such attacks, one or more intermediary systems that act as launch points or attack platforms are first compromised or infiltrated. The systems in between are frequently known as secondary victims, and they become infected with remote-control tools, which are commonly referred to as bots, zombies, or agents, by the attacker. Subsequently, either in accordance with a pre-determined schedule or triggered by a launch command from the attacker, the victim is subjected to a DoS attack as depicted in figure. Consequently, the victim may detect the zombified system(s) responsible for the DoS attack, but it's unlikely that they'll be able to locate the attacker behind it. In recent times, the practice of installing multiple bots or zombies on numerous unsuspecting secondary victims has been given the term "botnets" (as explained in the previous section titled "Botnets").
Distributed Reflective Denial of Service (DRDoS)
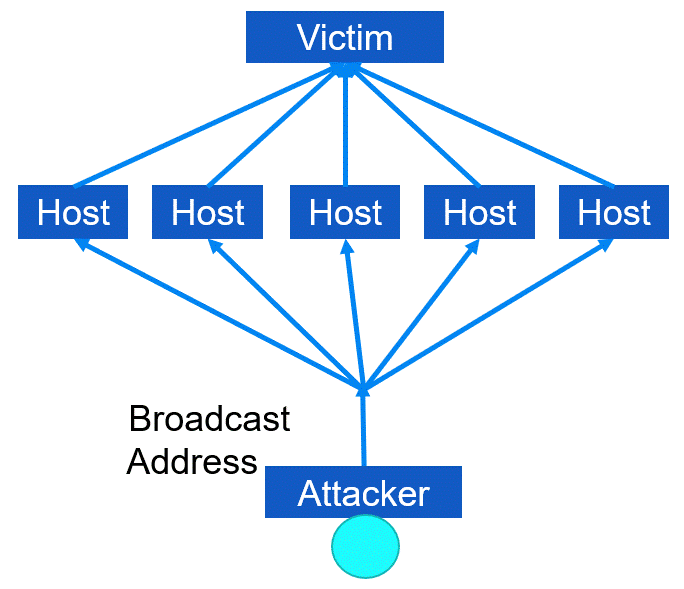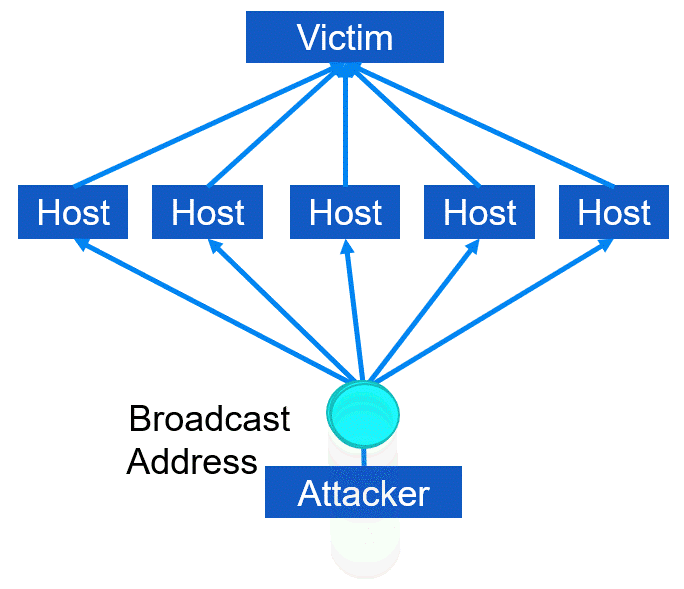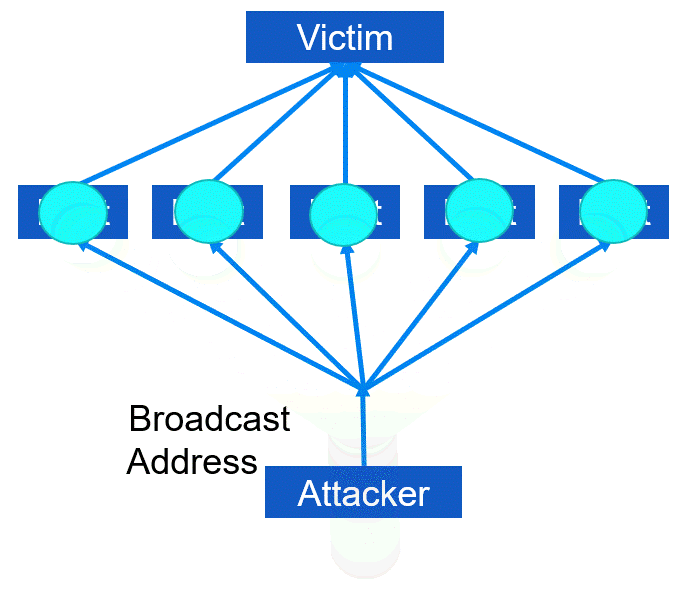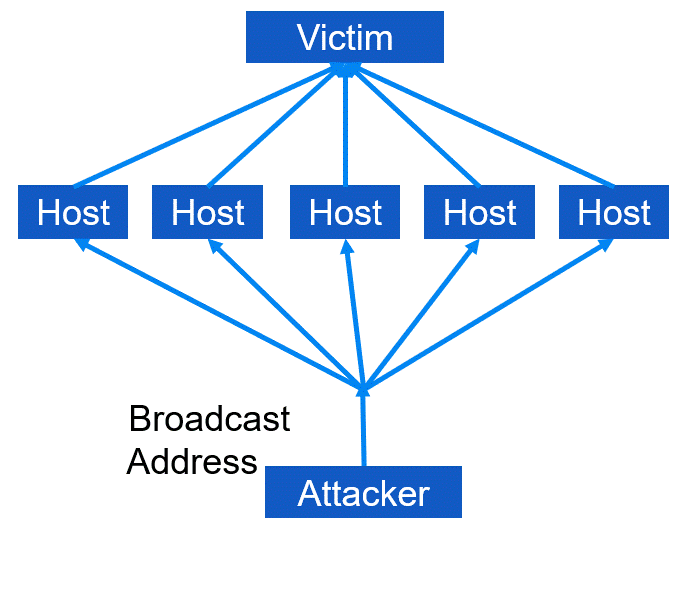
Aside from Denial of Service (DoS) and Distributed Denial of Service (DDoS), there exists another variant known as Distributed Reflective denial of service (DRDoS). This type of attack involves utilizing an amplification or bounce network that unwittingly receives broadcast messages and generates message responses, echoes, or bounces. The attacker effectively sends spoofed message packets to the broadcast address of the amplification network. As a result, every incoming packet received is transmitted to all hosts within that network, which may range from 10,000 to 100,000. Upon receiving each packet, every host generates a response. However, since the original packet's source was manipulated, the response is directed towards the victim rather than the actual sender (i.e., the attacker). As a result of this process, a single packet sent by the attacker is converted into numerous packets that exit the amplification network and flood the victim's communication link.
Techniques and Tools
Several specific tools and techniques exist for carrying out DoS, DDoS, and DRDoS attacks. Below are a few examples that you should be familiar with:
Smurf
In this type of DRDoS attack, the attacker employs ICMP echo reply packets (also known as ping packets). They send Type 8 ICMP echo request packets to the broadcast addresses of various intermediary networks while setting the source IP address as that of the primary victim. As a result of the attack, the victim receives multiple Type 0 ICMP replies, and this technique is referred to as a smurf attack, which is a type of amplification attack. Please refer to the Figure below for an illustration.
Fraggle
The Fraggle attack is a type of DRDoS that involves the use of UDP packets that are usually targeted towards port 7 (echo port) or port 19 (chargen or character generator port).
SYN flood
This attack involves exploiting the TCP three-way handshake, which is the process by which every TCP session begins. During this process, the client sends a SYN (synchronize) packet to the server, which responds with a SYN/ACK (synchronize/acknowledgment) packet, and the client then sends a final ACK packet. In this attack, the attacker impersonates a client and sends a large number of SYN packets but deliberately refrains from sending any final ACK packets. This causes the server to open various incomplete communication sessions, thereby exhausting all available network resources. The figure below illustrates SYN flood attack.
Ping of death
The attacker sends ping packets to the victim that exceed the standard size limit. Since the victim is not equipped to handle such invalid packets, it becomes overwhelmed and may experience freezing or crashing.
Xmas attack
The event referred to as the "Xmas attack" is, in reality, a type of port scanning known as the "Xmas scan". This method is commonly used by various port scanners, such as Nmap, Xprobe, and hping2. Essentially, the Xmas scan involves transmitting a TCP packet to a specified port, with the URG, PSH, and FIN flags all activated. By activating the URG, PSH, and FIN flags in the TCP packet, the resulting flag byte in the TCP header is 00101001. This particular configuration is said to resemble the blinking lights of a Christmas tree.
As per the TCP specifications, if a port is open, it should disregard any malformed packets, but if the port is closed, it will send an RST signal in response. With the exception of Windows operating systems, most systems follow the convention of responding to invalid packets by ignoring them if the port is open or sending an RST signal if the port is closed. In contrast, Windows operating systems tend to send RST signals in response to a variety of malformed packets, even if the port is open.
To carry out an Xmas attack (or scan), an individual sends packets with Xmas flags to one or more ports on a computer. When the number of scanning packets reaches a significant level, it can adversely impact the targeted system's performance or exhaust the available bandwidth. As a result, an Xmas scan has the potential to escalate to a denial of service (DoS) attack and, therefore, be classified as an Xmas attack.
The following types of attacks - SYN floods, teardrops, land attacks, ping floods, pings of death, bonks, and boinks - are typically classified as denial of service (DoS) attacks. However, if an attacker gains control of several intermediary systems and employs them to launch attacks on the victim, these attacks can be executed as distributed denial of service (DDoS) attacks. Fortunately, modern versions of protocols implemented in operating systems are equipped to automatically handle most basic DoS attacks that exploit error-handling procedures, such as ping of death, land attack, teardrop, bonk, boink, and others. However, protecting against many of the current distributed denial of service (DDoS) and distributed reflective denial of service (DRDoS) attacks is not as straightforward.
Measures and Precautions
Listed below are some measures and precautions to protect against these attacks:
- Collaborate with your internet service provider (ISP) to develop a response plan.
- Deploy firewalls, routers, and intrusion detection systems (IDSs) that can identify DoS traffic and either block the corresponding port or filter out packets based on the source or destination address.
- Deactivate the echo reply functionality on external systems.
- Turn off broadcast capabilities on border systems.
- Prevent forged(spoofed) packets from entering or exiting your network.
- Ensure that all systems are up to date with the latest security patches released by the vendors.
Regrettably, just as security professionals devise more robust safeguards, mitigations, and detection mechanisms to counter the diverse types of DoS attacks, attackers are simultaneously devising new ways and tactics to circumvent these protections.
Test Yourself
Take Free Quiz
Watch our Video Tutorial