SHREE LEARNING ACADEMY
Hijacking Attacks
Hijack attacks refer to instances where a malicious actor seizes control of a session that belongs to an authorized user. Depending on the specific method employed, certain forms of hijacking can cause the client to lose their connection, while others may allow the attacker to establish a separate connection to the targeted system or service. Let's see of these hijacking techniques.
Clickjacking
Clickjacking refers to a type of attack that occurs on a webpage and results in the user's click being directed to a different location than they intended. This can be achieved through the use of hidden or invisible overlays, frame sets, or image maps. If a user encounters an item or link on a webpage and clicks on it, an invisible or hidden layer can intercept the click, causing the request to be directed towards a destination other than what the user originally intended.
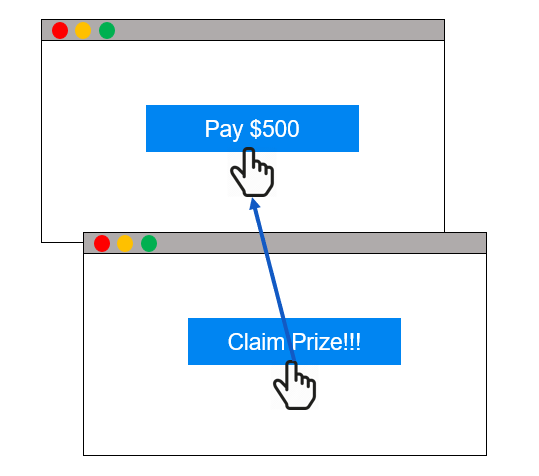
Clickjacking has the potential to facilitate various types of attacks, such as phishing, hijacking, Man-in-the-Middle (MitM), and Man-in-the-Browser (MitB). There are numerous instances of clickjacking, such as disguising an Amazon Buy button behind a Play button image, luring users into enabling their microphone or web camera, causing users to make their social media profiles public, downloading malicious software (such as backdoors, rootkits, and ransomware), and generating fake advertisement clicks.
Session hijacking
Session hijacking, also known as TCP/IP hijacking, is a type of attack in which an intruder gains control of an ongoing communication session. The attacker can take on the identity of either the client or server, depending on their objectives. Typically, during session hijacking, the other party involved in the communication (usually the client) is disconnected from the session. As a result, they become aware that the communication has been disrupted and that the session has been interrupted. Nevertheless, the affected party may not immediately recognize that they were unintentionally involved in a session hijacking attack. Several tools can be utilized to execute session hijacking, including Ettercap, Cain, Juggernaut, and Hunt.
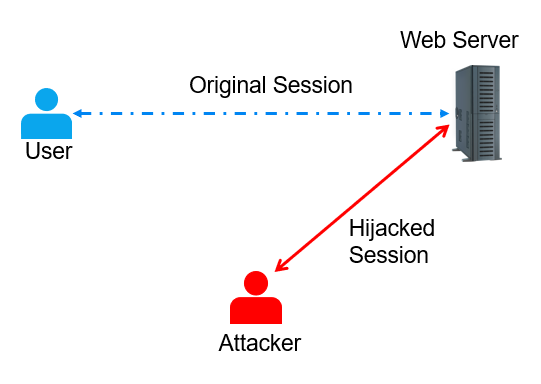
To prevent TCP/IP hijacking attacks, countermeasures include implementing encrypted protocols and conducting mid-stream reauthentication at regular intervals throughout the session. Furthermore, modern and secure protocols often incorporate preventative measures that make it extremely challenging, if not impossible, to execute session hijacking. These features consist of robust nonlinear sequencing regulations along with short timeout values for time stamps.
URL hijacking
URL hijacking, also known as typo squatting, is a tactic utilized to capture traffic generated by users who mistakenly enter an incorrect domain name or IP address while attempting to access a particular resource. A squatter anticipates URL typos and registers those domain names, directing the resulting traffic to their own website. URL hijacking can be carried out for competitive purposes or with malicious intent. Common types of variations employed in typo squatting include misspellings (such as googel.com), typing errors (such as gooogle.com), alterations of a name or word (for instance, plurality, as in googles.com), and utilization of different top-level domains (such as google.org).
The phrase URL hijacking can also refer to the act of showcasing a hyperlink or advertisement that resembles a recognized product, service, or website. However, once the user clicks on the link, they are redirected to a different location, service, or product. This can be achieved through various means, such as creating websites and pages and utilizing SEO (search engine optimization) techniques to increase the visibility of the content in search results. Alternatively, adware may be employed to replace authentic ads and links with those that direct users to alternate or malicious locations.
Domain hijacking
Domain hijacking, also referred to as domain theft, is a nefarious act that involves altering the registration of a domain name without the explicit consent of its legitimate owner. This can be carried out in a number of ways, such as stealing the owner's login credentials, leveraging XSRF, session hijacking, or MitM attacks, or exploiting a vulnerability in the domain registrar's systems.
Occasionally, when an individual registers a domain name right after the original owner's registration expires, it may be labeled as domain hijacking, but this isn't entirely accurate. While this may be deemed an unethical practice, it doesn't constitute an actual hack or attack. This practice entails exploiting the oversight of the initial owner's failure to manually renew their registration or configure auto-renewal. If an owner neglects to renew their domain registration, they may lose their domain name, and there may be no viable option other than to reach out to the new owner to inquire about regaining control. In such cases, many registrars implement a "you snooze, you lose" policy for expired registrations.
Losing control of their domain and having someone else take over can have a profound impact on an organization, its clients, and visitors. This could lead to the unavailability of the original website or online content, or it may not be accessible under the same domain name. The new proprietor has the ability to host entirely dissimilar content or even a deceitful replica of the previous website. This deceptive practice can deceive visitors, resembling a phishing scam, which could lead to the extraction and collection of personally identifiable information (PII).
Cookies
HTTP is referred to as a stateless protocol because it does not store any data regarding the previous interactions or history of requests made by a client. In essence, when a client, such as a web browser, sends a request to a web server via HTTP, the server treats the request as a discrete and separate event, with no knowledge of any prior requests made by the same client. This implies that each request is processed as a new and self-contained request, with no linkage or reference to previous requests made by the same client. Consequently, the server cannot recollect any data from past requests or sessions and must use additional methods like cookies or tokens to maintain continuity of stateful behavior over multiple requests.
A cookie is a technology used by web servers to track and respond to a user's sequential browsing of several web pages. Its primary purpose is to enable various functionalities such as preserving an e-commerce shopping cart, directing product display, or monitoring your website visit patterns. Unfortunately, the original benign intentions behind cookies have been perverted by malicious entities. Nowadays, cookies are often employed as a tool to invade your privacy by collecting data about your identity, login details, browsing tendencies, work routines, and other personal information.
A cookie can be easily misused against a web browser to acquire significant details about a user, which can enable an attacker to pose as the victim online. For this reason, it is usually advised to block third-party cookies from all sources, as well as first-party cookies from all but the most reputable websites. Typically, reputable websites are those that safeguard your identity by not including your personal information in a cookie. Instead, these websites only store a session ID in the cookie and maintain all your sensitive data in a backend database. Disabling trusted first-party cookies (also known as session cookies) will render certain features, such as e-commerce shopping carts, online banking, and posting to discussion forums, inaccessible.
Cookies may be exploited in a web service connection hijack, where the attacker establishes a separate connection while the legitimate user retains their connection. This is achieved by the attacker obtaining a copy of the cookie either during its transit between the legitimate client and server or by directly extracting it from the client's storage device. In case the cookie functions as an access token, the server will identify anyone holding it as the authenticated client who originally obtained it. The attacker installs the stolen cookie on their own system and utilizes their own web browser to access the targeted server. The server erroneously treats the attacker as another legitimate connection from the previously authenticated client. Websites ought to be constructed to identify and block multiple concurrent connections.
Test Yourself
Take Free Quiz
Watch our Video Tutorial

