SHREE LEARNING ACADEMY
Amplification Attack
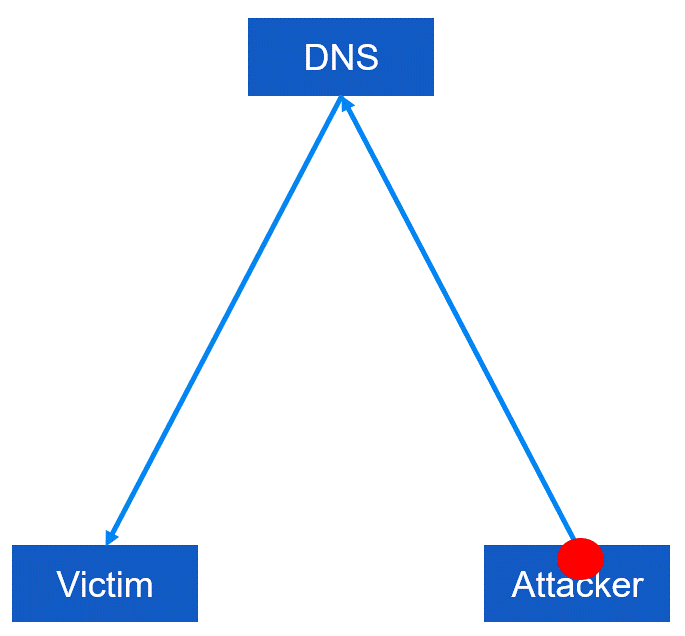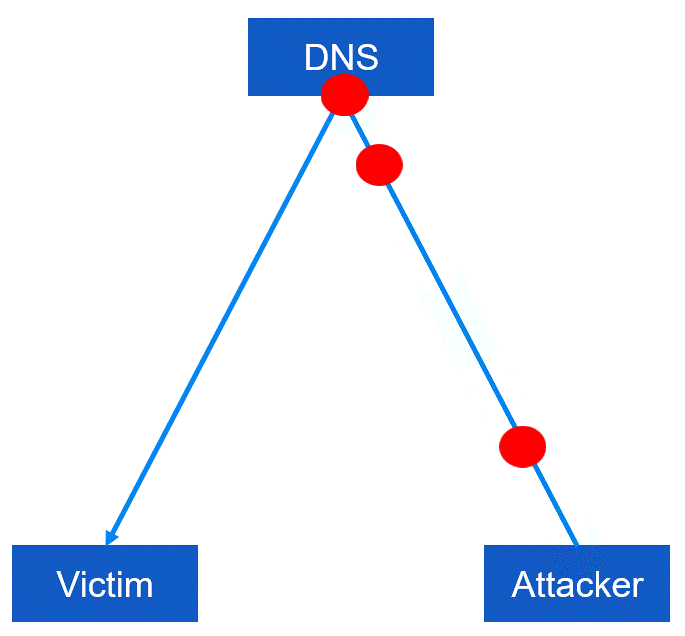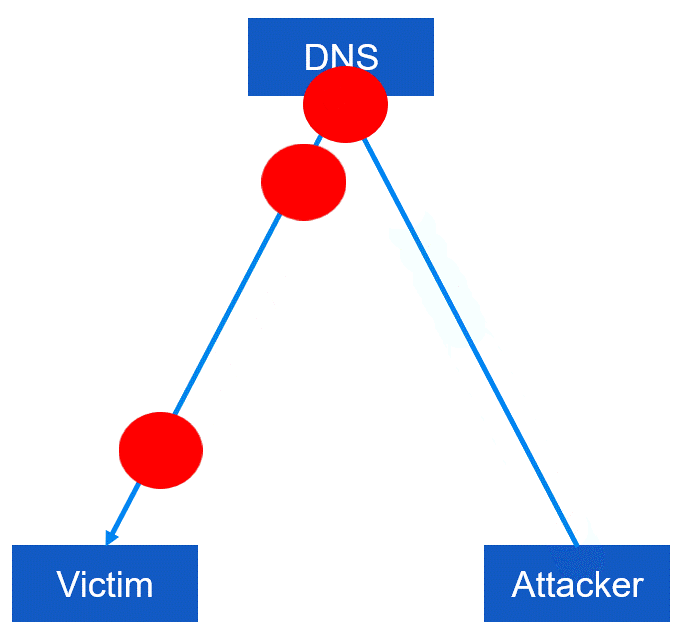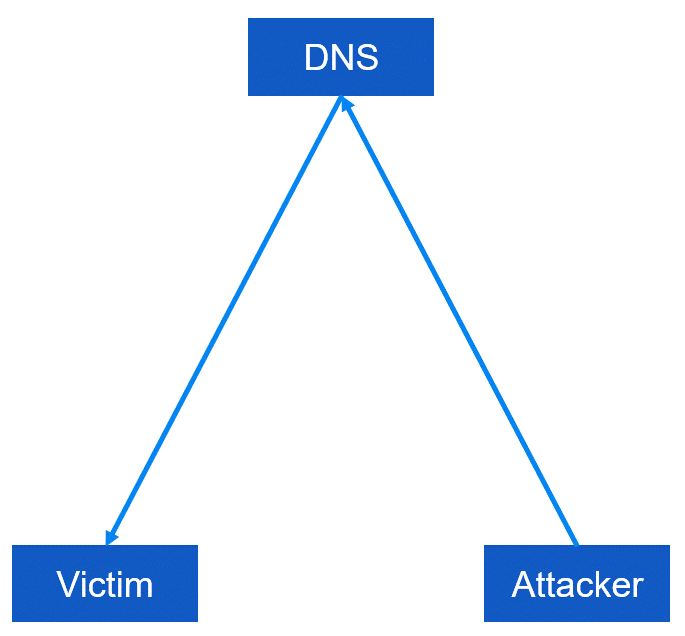
An Amplification Attack is a form of Distributed Reflective Denial of Service (DRDoS) attack(explained in previous chapter) that leverages a third-party server to magnify the volume of traffic directed towards a specific website or network. The attacker utilizes a falsified IP address, which appears to be the target's IP address, to send a series of small data packets to a server. This server, often an open DNS resolver or NTP server, then responds to these packets by sending a significantly larger amount of traffic towards the targeted website or network. The sheer volume of traffic can overwhelm the targeted system, resulting in a crash.
How Does an Amplification Attack Work?
To better understand the working of amplification attack, let's take a closer look at the steps involved in the attack:
Step 1: The attacker sends a small number of requests to an open DNS resolver or NTP server, using a spoofed IP address that appears to be the target's IP address.
Step 2: The server responds to the requests by sending a much larger amount of traffic to the target's IP address, which overwhelms the target's network and causes it to crash.
Step 3: The attacker repeats the process, sending more requests to the server and increasing the amount of traffic sent to the target.
Step 4: The targeted website or network becomes inaccessible to users, which can lead to a loss of revenue or other negative consequences.
Security Measures:
Now that we know what an amplification attack is and how it works, let's take a look at some ways to protect yourself from such attacks:
Use a Firewall:
Using a firewall is one of the most effective ways to protect against an amplification attack. You can do that by following these 2 steps:
1. Identify the Servers Used in Amplification Attacks:
In order to protect against an amplification attack, you first need to identify the servers that are commonly used in these attacks. You can do this by analyzing network traffic and looking for patterns of traffic that are commonly associated with amplification attacks. Once you have identified these servers, you can add them to your firewall's blacklist.
2. Configure Your Firewall to Block Traffic from Blacklisted Servers:
Once you have identified the servers used in amplification attacks, you need to configure your firewall to block traffic from these servers. You can do this by creating a rule in your firewall that blocks traffic from any IP addresses on the blacklist.
Disable Open Resolvers:
Open resolvers are DNS servers that allow anyone on the internet to query them. These servers can be easily exploited by attackers to amplify traffic and launch an amplification attack. It is important to ensure that your DNS server is not an open resolver, and instead, it should be configured to only respond to queries from authorized users. By disabling open resolvers, you can prevent attackers from exploiting your DNS server to launch an amplification attack.
Keep Software Up-to-Date:
Attackers often exploit known vulnerabilities in software and systems to launch cyberattacks. It is important to keep all software and systems up-to-date with the latest patches and updates to prevent attackers from exploiting known vulnerabilities. This includes operating systems, web servers, applications, and any other software or system components that are used on your network.
Use Rate Limiting:
Rate limiting is a technique that limits the amount of traffic that can be sent to your network or website. This can help prevent an amplification attack by limiting the number of responses that can be generated by the attacker. By setting a limit on the amount of traffic that can be sent to your network, you can prevent the attacker from overwhelming your network and causing it to crash.
Conclusion:
Amplification attacks are a significant threat to businesses and organizations, and it is important to take steps to protect yourself from these attacks. By using a firewall, disabling open resolvers, keeping software up-to-date, and using rate limiting, you can significantly reduce the risk of an amplification attack. It is important to stay vigilant and regularly assess your network security to ensure that you are protected against the latest threats.
Test Yourself
Take Free Quiz
Watch our Video Tutorial