SHREE LEARNING ACADEMY
Malware and its Types
Malware
If we look according to a legitimate user, then malware or malicious code is an element of software that performs unwanted functions. Malware is of many types and we are going to see some of those types.
Viruses
Viruses are an example of malware. The name of virus comes from biological viruses. They have been designed in such a way that they can spread from one system to another by self-replication and then perform malicious activities. Malicious activities that viruses can perform are data deletion, corruption, alteration and exfiltration. Some viruses replicate so much and so quickly that they eat up all the resources of the system, and then a type of DoS attack takes place. The full form of DoS is Denial of service which we will see in the next chapters.
Most viruses require a host so that it can attach/hook on them. Host can also be a file which is common in case of viruses. Or it can also be the boot sector of the storage device. Storage devices such as SSD, HDD, Blu-ray, CD / DVD-ROM, USB etc. If a virus gets attached in their boot sector, then it gets loaded in the memory as soon as that device is activated. This type of virus is called boot sector virus.
There are some other types of viruses like
Polymorphic viruses have the power to mask their code using encryption so that they can escape from an antivirus.
Macro viruses live inside documents and emails and exploit the scripting capabilities of productivity software such as word.
Stealth Viruses try to avoid detection by hiding their activities.
Armored viruses are a type of malware specially designed to avoid detection and are very difficult to remove. It uses complex compiling techniques and coding logic and abnormal usage of memory.
Retroviruses specially target the antivirus system so that it can be useless, that is why they are also called anti-antivirus.
Phage viruses modify or infect many parts of the system so that they can regenerate themselves from any remaining unremoved parts.
Companion Viruses renames itself from the root name of a common executable file and then puts a ".com" extension at the end so that it can be launched instead of a legitimate file.
Multipart or multipartite viruses can perform multiple tasks so that it can infect the system in many ways.
The best technology to avoid viruses is Antivirus at the home level and EDR at the enterprise level which are updated continuously and they monitor all local storage devices, communication pathways and memory from all viral activities. But one more thing that should be kept in mind is that the behaviour of the user should be changed so that he/she can avoid risky activities. Because if we do not reduce the human risk, then no technical protection can save us. Some examples that reduce the risk are, not downloading software from non-vendor sources, not opening unknown email attachments, and not using untrusted system's removable media.
If a system is infected with a virus, then some symptoms can be seen such as corrupted or missing files, applications that do not execute, slowness of the system, lag between mouse click and system response, application or system crash etc. Such symptoms can indicate virus infection, although those symptoms can also be of other malware infection.
Crypto-malware
Crypto-malware is a form of malware that uses cryptography as a weapon or defence. Crypto as a weapon in ransomware attack and crypto as a defence in polymorphic and Armored viruses.
Another use of crypto-malware is that it sends the keys of encrypted storage to the remote attacker. In this, the main goal is to give access of protected content to the attacker.
Symptoms of Crypto-malware can be, not being able to access the data, missing data, system which is not booting, pop-ups which are asking for payment so that you can decrypt the data.
Ransomware
Ransomware is a malware that encrypts the user data of your computer system so that you cannot access your data and neither you can delete the ransomware and hence it can charge money from you in exchange for your data. Usually, hackers who request for ransomware payment take money in an untraceable format like Bitcoin.
To avoid Ransomware, you can avoid risky behaviours, run anti-malware software, and maintain a proper backup of your data.
If in any way you are not able to recover the data, then only think of giving ransom, otherwise avoid paying ransom. Because by giving ransom, you are only motivating the attackers that they may do such attacks in future.
Symptoms of Ransomware can be not being able to access data, missing data, system that is not booting, slow system (usually during the encryption process), and pop-ups that demand payment so that they can decrypt and give your data.
Worm
Another malware which is slightly related to virus is worm. Worms are self-contained, that is, they do not require a host file like a virus. Generally, worms focus on replication and distribution rather than directly damaging the system. Worms have been designed to exploit a vulnerability of the system and then use that vulnerability to spread themselves. Worms are used to put viruses, logic bombs, backdoors, ransomware, bots in the system. Or worms can also cause direct damage just like viruses.
To avoid worms, you can take all the same measures that you take at the time of virus, such as running antivirus, keeping the system patched, keeping user behaviour aligned towards security, etc.
Symptoms of worm infection are slow responsive system, applications that does not execute, no free space in storage devices, CPU and memory utilization at 100%, and system crashes.
Trojan
Trojan horse is a type of malicious software that disguises itself using a legitimate file. The most common forms of Trojan horses are games and screensavers. But we can convert any software into trojan horse. The main goal of Trojan horse is to trick the user so that he can install it. And then the malicious part of that software which has trojan horse will get access to the user's secure environment. We can make a trojan horse by blending legitimate host file and malicious payload. And then together we can also use social engineering to trick the user. At the last, the victim gets tricked and accepts the trojan by thinking it is a legit file. And then when this file is executed, the malicious payload is released so that it can infect the system. Trojans generally install distributed denial of service (DDoS), remote control backdoors, or botnets into the system.
The name trojan horse came into the picture based on an ancient greek story. According to legend, the Greeks utilized a wooden horse, known as the Trojan Horse, as a strategic ploy to gain entry into the city of Troy and ultimately secure victory in the Trojan War. The Greeks built a colossal wooden horse and concealed a select group of soldiers inside. They then made it appear as though they were departing, leaving the horse behind as a symbol of their defeat and a victory trophy for the Trojans. The Trojans, believing they had won the war, triumphantly pulled the horse into their city. That night, the Greek soldiers emerged from the horse and opened the city gates for the remainder of the Greek army, which had returned under the cover of darkness. Subsequently, the Greeks seized the opportunity and destroyed Troy, bringing an end to the prolonged conflict. Modern trojan malware also uses this same strategy to get into our systems.

The measures we take to avoid virus can be taken to avoid trojans too.
The symptoms of any other malware that we have seen are true for trojan horse also.
Rootkit
Rootkit is a special type of malware that embeds itself very deep in the operating system. Rootkit positions itself in the heart of the operating system and then in this way it can manipulate all the information that the operating system sees. Mostly rootkit replaces the kernel of the OS and then inserts itself under the kernel, replaces the device drivers, or penetrates inside the application libraries so that whatever information it feeds or hides, The operating system thinks that it is normal and allowable. Because of this rootkit can hide itself from detection, can block file management tools from reading its files, and can block task or process management tools from seeing its processes. That is why we can say that rootkit has the power of invisibility. We can also use rootkit to hide other malware tools. Rootkit or other malicious tools that have been hidden by rootkit can capture keystrokes, sneak credentials, read URLs, capture screenshots, record mic, trace application use, or grant backdoor access to a remote hacker.
When any system gets infected with rootkit, then we cannot again trust that it is secure. There are some rootkits which have not yet been detected and removed. That's why we cannot fully trust any rootkit-infected system. For example, if you are fighting with an invisible army, then how can you be sure that you have defeated all the soldiers?
There are some rootkit detection tools, some of which can also remove rootkit. But once you suspect that there is a rootkit in your system, then a really secure way to respond is to either reconstitute your system or replace the entire computer. Reconstitution means performing low-level formatting on all storage devices connected to this system, reinstalling the operating system, re-downloading all applications from trusted sources, and restoring files from trusted rootkit-free backups. clearly, the best way against rootkits is defence and not response because, some responses are not reliable and some are not feasible.
Mostly there are no noticeable symptoms related to rootkits because the developers of rootkit keep in mind that no one can notice it when it is being executed or installed. But still system slowness can be seen in initial stage of rootkit installation, rest once rootkit has taken over, after that it will mask all the symptoms.
Keylogger
Keylogger is a malware that records keystrokes, whatever you enter from the keyboard of the system. Software keyloggers can record both physical and on-screen keyboard. The keystrokes that are captured are then sent to the attacker so that he can analyze and exploit them.
Many anti-malware scanners also include the signatures of keyloggers, although a Potentially Unwanted Program (PUP) scanner such as Malwarebytes may also be necessary to detect this type of software.
Hardware keyloggers are physical devices that are connected to your keyboard cable where there is a connection between the cable and the main system. Such devices are not detected by software and for this physical checking is required. Some hardware keyloggers can upload data over WiFi, Bluetooth, or cellular service, and some keyloggers have to be physically recovered.
Symptoms of a keylogger can be slower keyboard response, the need to type keys twice, and degradation of system performance.
Spyware
Spyware is a type of malicious code or business or commercial code that collects users information without their knowledge or permission. Spyware can perform complete malicious activity if it needs information to perform identity theft or credential hijacking. However, many advertising companies use less malicious form of spyware so that they can collect demographics of their customers. In any case, the user does not know that any spyware tool is present in their system and it is continuously gathering the information and sending it to someone every now and then. Spyware can collect keystrokes, names of executing processes, files stored, emails, instant messages, URLs, record through mic or camera.
Spyware can be deposited via viruses, trojan horses, worms or they can be installed with any freeware or shareware application.
To avoid spyware, you can use all those measures which you do to avoid virus and also you can use spyware scanners.
Symptoms of Spyware can be slow performance, getting unknown files in the system, free storage ending quickly.
Adware
Adware is a type of spyware that presents users with pop-up advertisements according to their online activities, visited URLs, accessed applications, and other factors. The purpose of adware is to tailor advertisements to potential customers. Sadly, the majority of adware applications are installed on client systems without the user's knowledge or consent. As a result, even legitimate commercial products are often perceived as intrusive and malicious adware.
Certain types of adware showcase counterfeit or deceitful security products. These adware programs may show an animation that mimics a system scan, and try to make you feel that they are looking for instances of malicious code or intrusion events. However, they are not. Later the scan, the adware exhibits a warning indicating the presence of issues and proposes a solution which is to install their software to remove these hoax malware that they found. Their software can be both free or paid and may contain additional malware to infect your system.
The preventive measures against adware are similar to those of spyware and viruses, which entail employing anti-malware software that is equipped with specialized scanning tools designed to detect spyware/adware.
Signs of adware intrusion may consist of ads appearing in pop-up form even without the web browser being active, slow system performance, and unresponsive mouse movements, particularly when clicking on links.
Botnet
Botnet is a term derived from "robot network" and refers to a large-scale distribution of harmful software onto multiple compromised systems that are under the remote control of a hacker. The concept of a botnet combines traditional DoS attacks to form a distributed denial-of-service (DDoS) attack. In a DDoS attack, the attacker plants remote-controlled agents, zombies, or bots on multiple secondary victims, and utilizes them as a unified entity to launch an attack on a primary target.
A hacker is responsible for the direct or indirect control of botnets, and may go by various names such as bot herder, master, or handler. Direct control is exercised when the bot herder transmits commands to individual bots within the botnet.
Consequently, bots are programmed to have a listening service that is active on an open port, expecting communication from the bot herder. Alternatively, indirect control of a botnet can be established through various intermediary communication systems, such as Internet Relay Chat (IRC), instant messaging (IM), email, File Transfer Protocol (FTP), social media platforms like Facebook, Twitter, blogging, or even the Web.
In scenarios where indirect control is employed, the bots connect to an intermediary communication service to receive messages from the bot herder. This intermediary communication service is commonly referred to as a "command and control center." However, rather than functioning as a complex controlling interface, it serves as a central point of connection between the attacker and the bots where information is exchanged.
Botnets are made possible due to the widespread accessibility of computers over the Internet, coupled with weak security measures in place on many of these systems. To create a botnet, the botnet creator develops code that exploits common vulnerabilities, and leverages techniques similar to those used by viruses, worms, and Trojan horses to propagate the botnet agent across a large number of systems. Botnets typically consist of numerous secondary victims, sometimes numbering in the thousands or even hundreds of thousands. The secondary victims serve as the hosts for the botnet agent, but are not impacted beyond the initial infiltration and installation of the botnet agent. This is because the hackers want the secondary victims to remain functional so that they can harness their resources when launching the botnet attack against the primary victim.
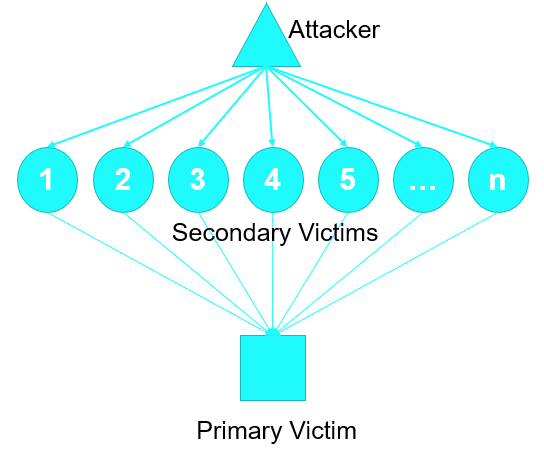
Botnets can be employed to carry out a wide range of malicious activities. While they are primarily associated with DoS flooding attacks, they can also be used for other purposes such as transmitting spam, performing highly distributed parallel processing to crack passwords or encryption keys, launching phishing attacks, capturing network packets, and executing any other malicious activity that can be imagined.
To effectively guard against a botnet attack, it is important to maintain patched and hardened systems and to avoid becoming the host of a botnet agent that is, avoid becoming a secondary victim. Employing strict outbound firewall rules, spoofed source address filtering, and web content filtering via a unified threat management (UTM) device can also serve as effective preventive measures. Additionally, most antivirus software and antispyware/adware tools have incorporated well-known botnet agents into their detection databases.
When it comes to being the primary victim of a botnet flooding attack, there are limited options available to stop the attack. Typically, the most effective responses include disconnecting from the internet, notifying your Internet Service Provider (ISP), and reporting the incident to law enforcement. There are various DDoS filtering services available, ranging from free to expensive enterprise-class services.
Signs of a botnet attack may include sluggish system performance, high levels of CPU and memory usage, unusual network traffic, the appearance of unfamiliar files on storage devices, the presence of unknown running processes, and the appearance of unfamiliar program windows on the desktop.
RAT
A Remote-Access Trojan (RAT) is a form of malware that allows attackers to gain remote control over a compromised system. Frequently, the backdoor component for remote control is concealed within a host file that is associated with a popular trend, such as a new movie, music album, or game. When the victim opens the host file, the remote-control malware installs on their system, and a notification is transmitted to the attacker. In most cases, RATs create an outbound connection to the attacker's system, which enables them to manipulate the victim's data and system operations.
RAT infections can cause various symptoms such as unusual network traffic, a system that fails to activate the screensaver or timed sleep mode, increased activity in the drive, CPU, and memory, and unfamiliar files appearing on storage devices.
Logic Bomb
A logic bomb is a type of malware that remains inactive until a particular event occurs. The event that triggers it could be a specific time and date, the launch of a particular program, the input of a particular key combination, or the access of a particular URL, such as the login page of your bank. The possible harmful actions that logic bombs can execute are numerous, as they can be programmed to perform any malicious function the creator desires, ranging from crashing systems, to deleting data, modifying configurations, and even stealing credentials used for authentication.
A logic bomb can also manifest as a fork bomb, which initiates a duplication process where the original code is replicated and executed. Subsequently, each of these new copies generates further duplicates of itself. The forking/cloning process continues until the malware consumes all available resources, leading to system failure. Additionally, a fork bomb can exhaust storage space or deplete network bandwidth as part of its operation.
Signs of a logic bomb attack may include sudden shifts in system performance, a decrease in the amount of available storage space on devices, and application or system crashes.
Backdoor
There are two distinct meanings associated with the term "backdoor" when it comes to system vulnerabilities or attacks. The initial and most ancient form of backdoor involved a secret entry point that developers would install, to bypass any security measures in place. A backdoor is a means of accessing a computer system, application, or network without going through normal security measures. It can take the form of a hard-coded user account, password, or command sequence that enables anyone with knowledge of the access hook also known as a maintenance hook to gain entry to the environment and make modifications.
From a developer's point of view, this may seem like a useful approach, especially during the coding and debugging phases. However, these programming shortcuts are frequently overlooked as the product approaches completion, resulting in their inclusion in the final product. If a backdoor is identified in a product that has already been released, the vendor typically issues a patch to eliminate the backdoor code from the installed product. Keeping up with updates and patches released by the vendor is a wise move, as the potential existence of backdoors is another compelling reason to do so.
The term backdoor also refers to a remote-access client that is installed by hackers. These harmful tools are small in size and can be implanted on a computer through various means, such as a Trojan horse, a worm, a virus, downloads of mobile code from websites, and as part of an intrusion attempt. Once a malicious tool is operational on a system, it creates open access ports and awaits incoming connections. As a result, a backdoor functions as an entry point for hackers, enabling them to circumvent any security measures and obtain or regain access to a system.
Back Orifice, NetBus, and Sub7 are among the frequently used backdoor tools designed for the Windows operating system. However, virus scanners and spyware scanning tools are capable of identifying and eliminating these and other similar backdoor tools.
To prevent backdoors, it is advisable to take precautionary measures such as limiting the automatic downloading of mobile code to your systems, implementing software policies to disallow the installation of unauthorized software, monitoring both incoming and outgoing traffic, and making software and driver signing a mandatory requirement.
If a backdoor has been compromised, you may observe various noticeable indications, including an unresponsive system, applications that appear to be opening or closing on their own, unusual network connections and activity, and the presence of new or missing files.
Test Yourself
Take Free Quiz
Watch our Video Tutorial

