SHREE LEARNING ACADEMY
DNS Poisoning
The manipulation of DNS information to misdirect a client's access to a specific system is known as DNS poisoning, which can occur through various methods. Whenever a client attempts to translate a DNS name into an IP address, it typically goes through the following steps:
- Verify the local cache, which includes data from the HOSTS file.
-
Transmit a DNS query to a recognized DNS server.
- Broadcast a query to any potential DNS server on the local subnet. (Note that this step is not universally supported.)
In the event that the client is unable to obtain an IP address via DNS resolution from any of these methods, the resolution will fail and the communication cannot be transmitted. DNS poisoning can occur at any of these stages, but the simplest method involves tampering with either the HOSTS file or the DNS server query.
Techniques of exploitation
There exist numerous methods to attack or exploit DNS, and an attacker may utilize any of the following techniques:
DNS Spoofing:
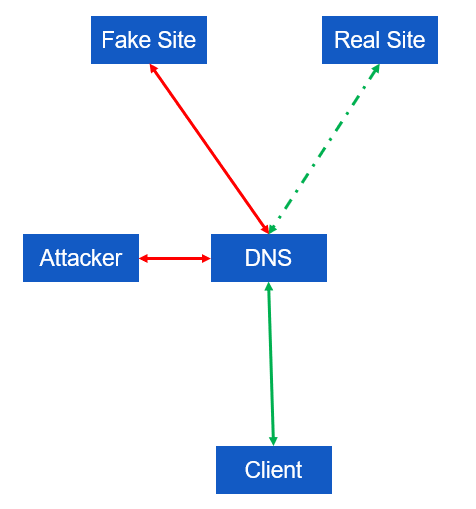
One method for attacking DNS is to utilize a rogue DNS server, which is also referred to as DNS spoofing or DNS pharming. A rogue DNS server has the ability to intercept network traffic, specifically DNS queries pertaining to a targeted site. It can then send a false IP address to the client by way of a DNS response. For this type of attack to be successful, the rogue DNS server must be able to transmit its response to the client before the legitimate DNS server responds. Upon receiving the response from the rogue DNS server, the client will terminate the DNS query session. Consequently, any response from the legitimate DNS server will be discarded as an out-of-session packet and disregarded.
Although DNS queries lack authentication, they do feature a 16-bit value referred to as the Query ID or QID. In order for a DNS response to be accepted, it must contain the same QID as the query. As such, a rogue DNS server must include the requesting QID in any false reply it generates.
Perform DNS poisoning:
DNS poisoning occurs when the legitimate DNS server is attacked and false information is inserted into its zone file. This prompts the real DNS server to distribute incorrect data to clients.
Alter the HOSTS file:
By manipulating the HOSTS file on a client and entering falsified DNS data, users will be redirected to erroneous locations.
Corrupt the IP configuration:
Tampering with the IP configuration can lead to a client being equipped with an incorrect DNS server definition. This can be achieved by altering the client's settings or by manipulating the network's DHCP server.
Use proxy falsification
This particular approach is limited to web-based communications. The attack involves inserting fabricated web proxy information into a client's browser, which allows the attacker to control a rogue proxy server. Through the use of a rogue proxy server, HTTP traffic packets can be modified in such a way as to redirect requests to any site of the attacker's choosing.
Security Measures:
While there exist various DNS poisoning methods, implementing some fundamental security measures can significantly diminish their potential impact. Here are a few examples:
- To mitigate the risk of DNS poisoning, one can restrict zone transfers from internal DNS servers to external DNS servers. This can be achieved by blocking inbound TCP port 53, which handles zone transfer requests, and UDP port 53, which manages queries.
- Restrict the external DNS servers from which internal DNS servers obtain zone transfers.
- Install a network intrusion detection system (NIDS) to monitor for unusual DNS traffic.
- Thoroughly secure all DNS, server, and client systems within your internal network.
- Employ DNSSEC to harden the security of your DNS infrastructure.
- Mandate that internal clients resolve all domain names through the internal DNS. To achieve this, it's necessary to block outbound UDP port 53 for queries, while keeping outbound TCP port 53 open for zone transfers.
DNS Pharming
DNS pharming is an attack that shares similarities with DNS poisoning and DNS spoofing, whereby a legitimate website's IP address or URL is redirected to a counterfeit site that contains a fraudulent version of the original content. This frequently occurs in phishing attacks, in which the attacker aims to deceive the target into revealing their login credentials. If the victims are not cautious or observant, they may inadvertently disclose their login details to the fraudulent website. Pharming commonly takes place through either altering the HOSTS file on a local system or by engaging in DNS poisoning or DNS spoofing. As hackers have found ways to exploit DNS vulnerabilities, pharming has become a more significant concern, as it allows them to phish numerous domain names for targeted groups of users.
Test Yourself
Take Free Quiz
Watch our Video Tutorial

