SHREE LEARNING ACADEMY
ARP Poisoning
ARP poisoning refers to the manipulation of the IP-to-MAC address resolution system utilized by TCP/IP. This is accomplished by interfering with the operation of ARP at the Data-Link layer, which is also known as Layer 2 in the OSI model.
Working of ARP
The task of ARP involves the conversion of IP addresses into MAC addresses, which enables Layer 2 to assign physical addresses to frames prior to transmission to the Physical layer (Layer 1). The process of ARP resolution is similar to that of DNS and involves multiple steps. When attempting to resolve an IP address into a MAC address via ARP, the system will first look into the local ARP cache. In case the IP-MAC mapping is not found in the cache, the system will proceed with an ARP broadcast.
The ARP broadcast involves transmitting a message to all potential recipients within the local subnet (or more precisely, all members of the same Ethernet broadcast domain, which typically includes the same set of systems as the local subnet). The message requests all hosts to identify if they possess the specified IP address. In case the system that owns the specified IP address is available within the network, it will reply directly to the source system by disclosing its MAC address.
The usage of MAC addresses is crucial in TCP/IP communication, as data transfers happen between host to host and router to router based not only on IP addresses but predominantly on MAC addresses. When a host sends data to another host within the same subnet, it utilizes its own MAC-addressed Network Interface Card (NIC) to transmit the signal directly to the target's MAC-addressed NIC. However, if the target is located in a different subnet, the host sends the message to the MAC-addressed NIC of the default gateway, which refers to the router interface in that particular subnet. Subsequently, the responsibility of finding the target host falls upon the router, which attempts to locate the host either within a subnet connected to one of its ports or by forwarding the message to another router that might have better connectivity to the target host's subnet. However, without appropriate ARP functioning, this process cannot be accomplished.
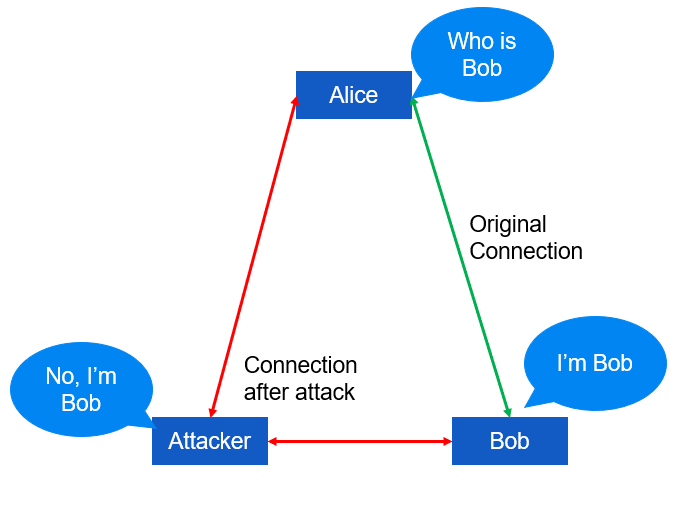
ARP Poisoning
ARP poisoning can occur in various ways, but the two most frequent methods are by corrupting the local ARP cache or by transmitting deceitful ARP replies or announcements. In either scenario, if a host obtains an erroneous MAC address for an IP address, there is a high probability that its transmission will be routed to the incorrect destination. While this technique is particularly successful within a single subnet, it also has a significant impact on multiple subnets. ARP poisoning is a popular approach employed in active sniffing attacks, where fake ARP announcements are utilized to reroute traffic to a system controlled by the hacker. This enables the attacker to gain access to the content of all transactions. To avoid a Denial of Service (DoS) scenario and maintain the illusion of normalcy, the attacker must ensure that each Ethernet frame is forwarded to the appropriate MAC address destination.

Prevention
Arpwatch is a widely used tool to detect ARP poisoning, but the most effective means of preventing ARP-based attacks, such as ARP poisoning, is implementing port security on the switch. By enabling switch port security, it is possible to prevent communication with unauthenticated, unknown or rogue devices, as well as identify the specific system that is responsible for answering to all ARP queries and stop it from sending any ARP replies.
Test Yourself
Take Free Quiz
Watch our Video Tutorial

